Find A Pattern By AWS Well Architected Pillar
The AWS Well-Architected Framework helps you understand the pros and cons of decisions you make while building systems on AWS. By using the Framework, you will learn architectural best practices for designing and operating reliable, secure, efficient, and cost-effective systems in the cloud. It provides a way for you to consistently measure your architectures against best practices and identify areas for improvement. We believe that having well-architected systems greatly increases the likelihood of business success.
The Five Pillars are:

OPS 1: How do you understand the health of your Serverless application?
Evaluating your metrics, distributed tracing, and logging gives you insight into business and operational events, and helps you understand which services should be optimized to improve your customer’s experience.
AWS DocsAWS Best Practices
1 / Understand, analyze, and alert on metrics provided out of the box:
Each managed service emits metrics out of the box. Establish key metrics for each managed service as the basis for comparison, and for identifying under and over performing components. Examples of key metrics include function errors, queue depth, failed state machine executions, and response times.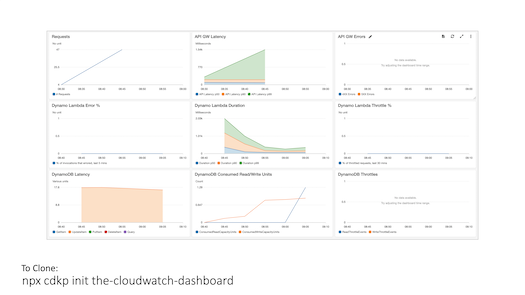
The CloudWatch Dashboard
Build and deploy a well architected CloudWatch dashboard with alerts for the simple webservice pattern
2 / Use distributed tracing and code is instrumented with additional context:
Instrument your application code to emit information about its status, correlation identifiers, business outcomes, and information to determine transaction flows across your workload.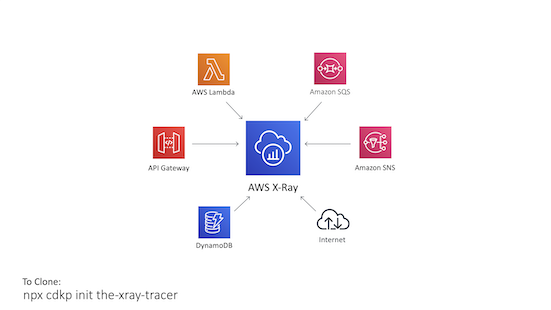
The X-Ray Tracer
Learn about using AWS X-Ray for tracing events through your system. This pattern has X-Ray enabled on API Gateway, Lambda, DynamoDB, External HTTP calls, SNS and SQS
3 / Use structured and centralized logging:
Standardize your application logging to emit operational information about transactions, correlation identifiers, request identifiers across components, and business outcomes. Use this information to answer arbitrary questions about the state of your workload.4 / Use application, business, and operations metrics:
Identify key performance indicators (KPIs) based on desired business and customer outcomes. Evaluate KPIs to determine workload success and operational health.OPS 2: How do you approach application lifecycle management?
Adopt lifecycle management approaches that improve the flow of changes to production with higher fidelity, fast feedback on quality, and quick bug fixing. These practices help you rapidly identify, remediate, and limit changes that impact customer experience.
All CDK Patterns use Infrastructure as code that enables you to create disposable environments through cdk deploy, then quickly destroy them through cdk destroy.
AWS Improvement Plan
SEC 1: How do you control access to your Serverless API?
Use authentication and authorization mechanisms to prevent unauthorized access, and enforce quotas for public resources.
AWS Docs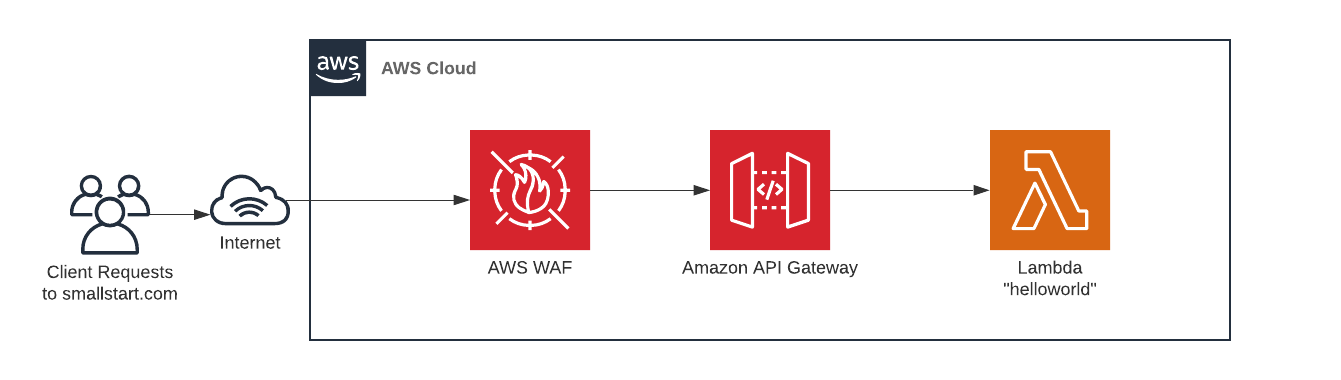
The WAF API Gateway
Add a Firewall infront of your public resources like API Gateway to increase the security of your application
SEC 2: How do you manage your Serverless application’s security boundaries?
Defining and securing your Serverless application’s boundaries ensures isolation for, within, and between components.
AWS DocsAWS Best Practices
1 / Evaluate and define resource policies:
Resource policies can restrict inbound access to managed services. Consider using resource policies to restrict access to your component based on the source IP address/range, geolocation, function event source, version, alias, queues, etc.2 / Use temporary credentials between resources and components:
Credentials and permissions policies should not be shared between any resources in order to maintain a granular segregation of permissions.
CDK out of the box does a great job defining IAM roles with least priviledge per function. You can however end up sharing roles if you are not careful,
you will notice that the unit tests for all cdk patterns check that the roles are not merged.
e.g. EventBridge ETL Lambda Permissions Unit Test
3 / Control network traffic at all layers:
Apply controls for controlling both ingress and egress traffic, including data loss prevention. Functions deployed to virtual private networks must consider network access restrict resource access.4 / Design smaller, single purpose functions:
Grant automated or programmatic access to users or roles with only the minimum privileges needed in order to reduce the risk of unauthorized access. Creating smaller, single purpose functions enables you to keep your permissions aligned to least privileged access, and reduces the risk of compromise since the function will do less.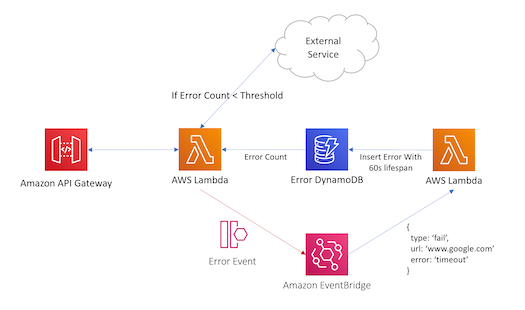
The EventBridge Circuit Breaker
The two lambdas in this pattern only have read or write access to DynamoDB, not both.
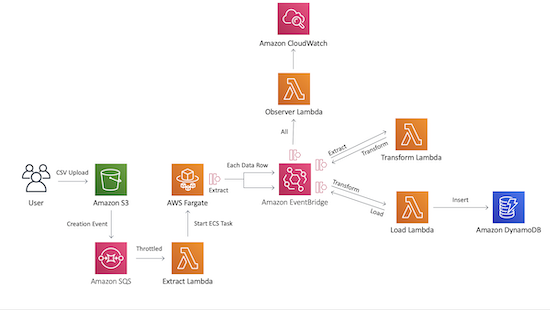
The EventBridge ETL
Each component in the ETL flow only has access to exactly what it needs
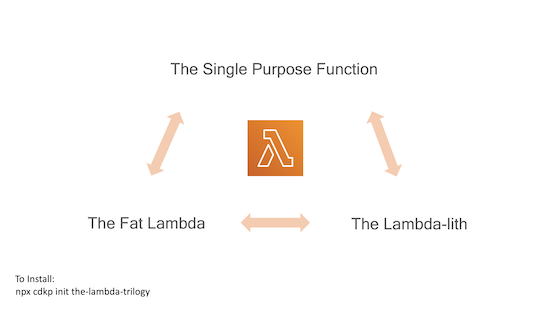
The Lambda Trilogy
See the difference in a single purpose function, a fat lambda and a lambdalith
SEC 3: How do you implement application Security in your workload?
Review and automate security practices at the application code level, and enforce security code review as part of development workflow. These best practices protect against emerging security threats and reduce the attack surface from malicious code (including third-party dependencies).
AWS Docs
REL 1: How are you regulating inbound request rates?
Defining, analyzing, and enforcing inbound request rates helps achieve better throughput. Regulation helps you adapt different scaling mechanisms based on customer demand.
AWS DocsAWS Best Practices
1 / Use throttling to control inbound request rates:
Use throttling limits to control inbound requests by setting steady-state and burst rates limits.
The EventBridge ETL
Every single lambda in this pattern is throttled down to prevent account level Lambda concurrency DOS
2 / Use, analyze, and enforce API quotas:
API quotas limit the maximum number of requests that can be submitted within a specified time interval with a given API key.3 / Use mechanisms to protect non-scalable resources:
Functions can scale faster than traditional resources, such as relational databases and cache systems. Protect non-scalable resources by adapting fast scaling components to downstream systems throughput.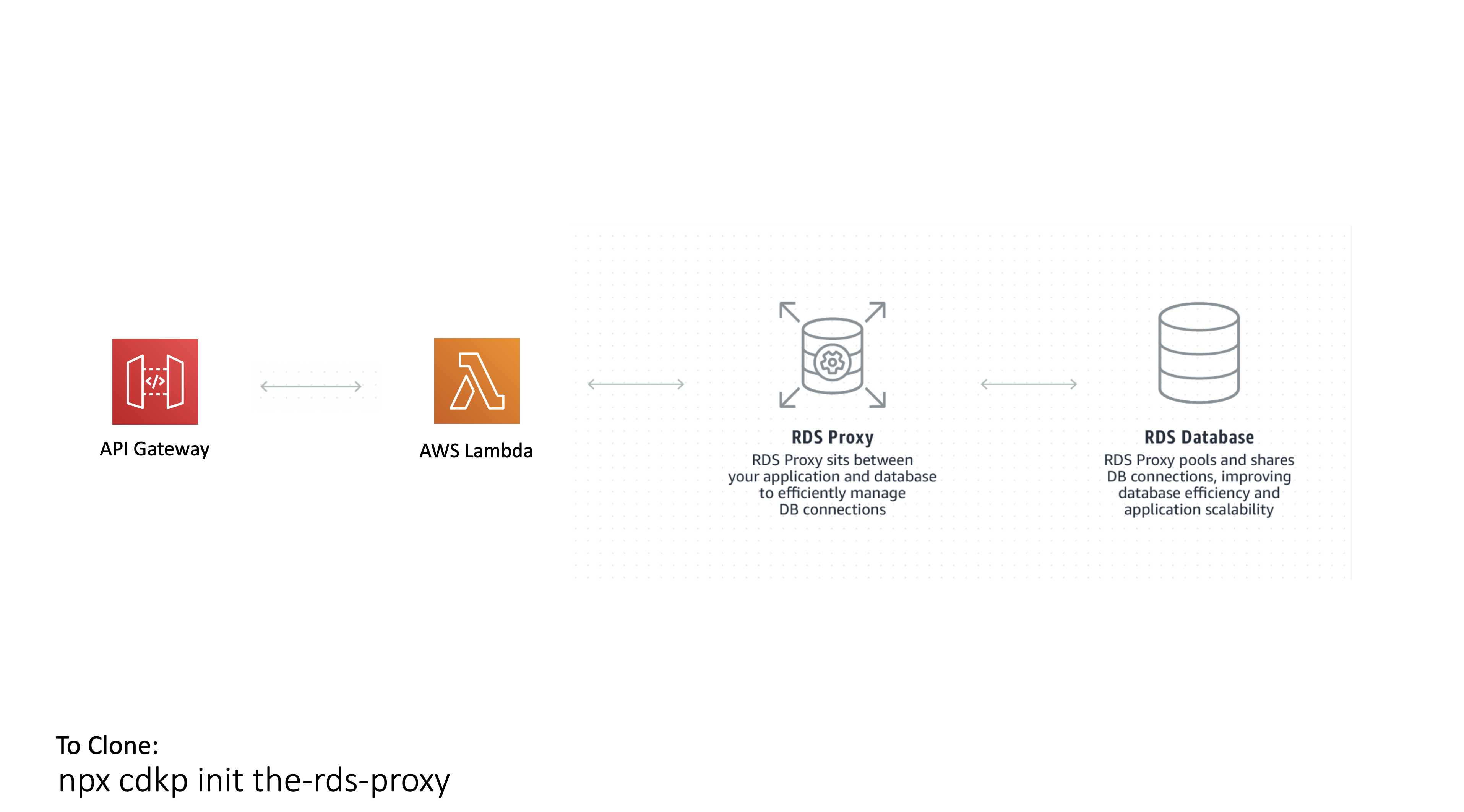
The RDS Proxy
Use RDS Proxy to protect a MySQL RDS Instance from the massively scalable Lambda Function querying it

The Scalable Webhook
Need to integrate a non serverless resource like RDS with a serverless one like Lambda? This is your pattern
REL 2: How are you building resiliency into your serverless application?
Evaluate scaling mechanisms for Serverless and non-Serverless resources to meet customer demand, and build resiliency to withstand partial and intermittent failures across dependencies.
AWS DocsAWS Best Practices
1 / Manage transaction, partial, and intermittent failures:
Transaction failures might occur when components are under high load. Partial failures can occur during batch processing, while intermittent failures might occur due to network or other transient issues.
The EventBridge Circuit Breaker
Integrate with unreliable external services? Build a circuit breaker and handle the risk
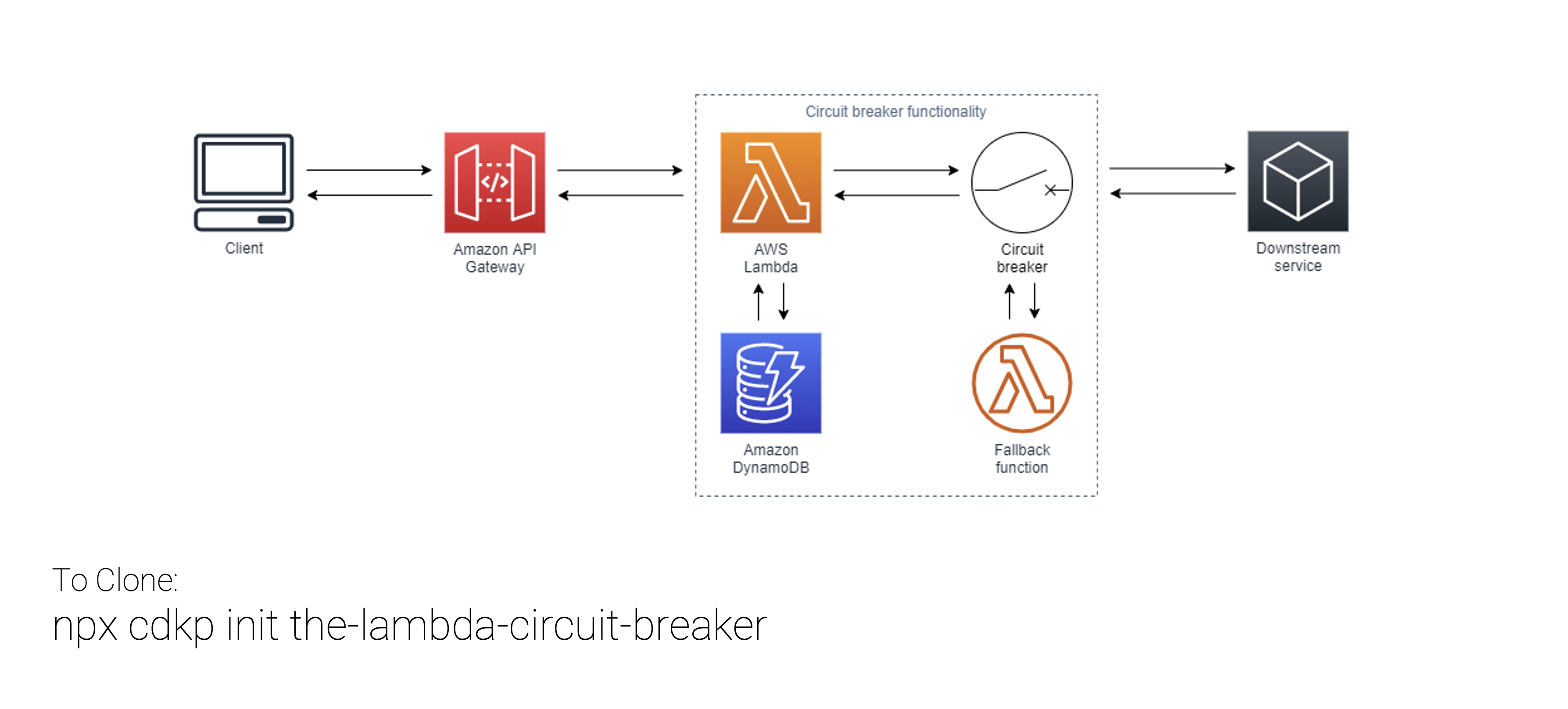
The Lambda Circuit Breaker
Deploy Gunnar Grosch's circuitbreaker-lambda inside a reference architecture to learn serverless resiliency
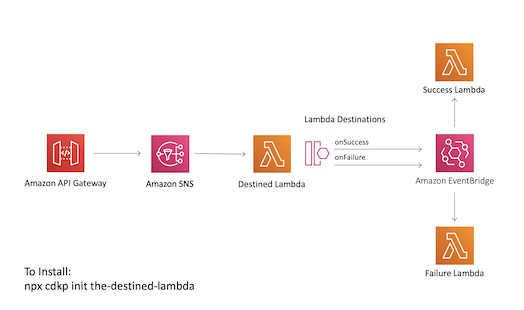
The Destined Lambda
Lambda Destinations give the full error trace as standard, allowing you to easily replay events
2 / Manage duplicate and unwanted events:
Duplicate events can occur when a request is retried, multiple consumers process the same message from a queue or stream, or when a request is sent twice at different time intervals with the same parameters. Design your applications to process multiple identical requests to have the same effect as making a single request. Events not adhering to your schema should be discarded.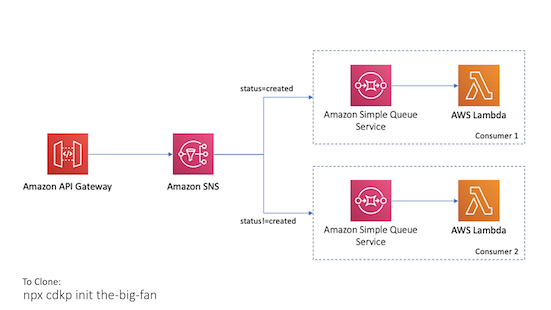
The Big Fan
Uses SNS event filtering to fan out specific events to different consumers
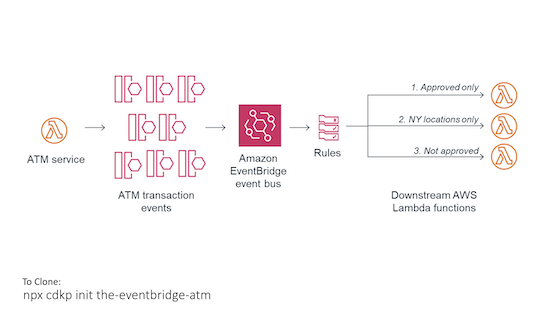
The EventBridge ATM
Build an event driven ATM with different rules to route events to different consumers

The Scalable Webhook
SQS frequently sends the same event twice so this pattern uses a Deduplication ID to handle that scenario
3 / Orchestrate long-running transactions:
Long-running transactions can be processed by one or multiple components. Favor state machines for long-running transaction instead of handling them within application code in a single component or multiple synchronous dependency call chains.
The EventBridge ETL
An alternative to step functions is to use EventBridge to handle complex flows asynchronously
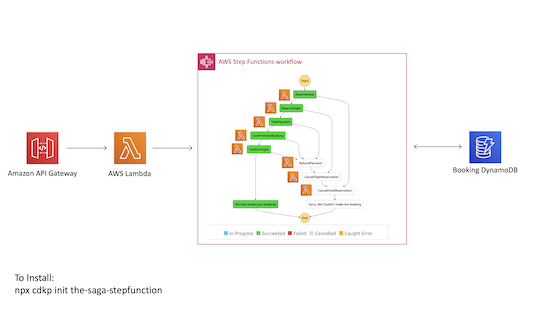
The Saga Step Function
A mechanism for handling distributed transactions within your system.
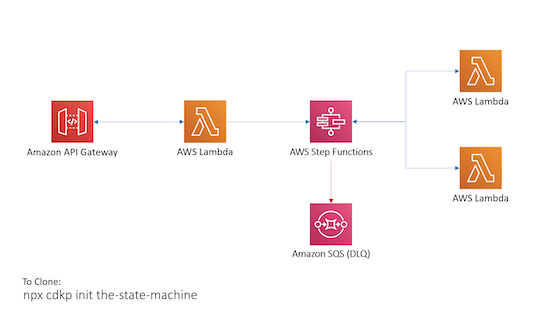
The State Machine
Have complex orchestration logic in your application? Build a state machine
4 / Consider scaling patterns at burst rates:
In addition to your baseline performance, consider evaluating how your workload handle initial burst rates that may be expected or unexpected peaks.
PER 1: How have you optimized the performance of your serverless application?
Evaluating and optimizing your Serverless application’s performance based on access patterns, scaling mechanisms, and native integrations allows you to continuously gain more value per transaction.
AWS DocsAWS Best Practices
1 / Measure, evaluate, and select optimum capacity units:
Capacity units can be function memory size, stream shards, database reads/writes request units, API endpoints, etc.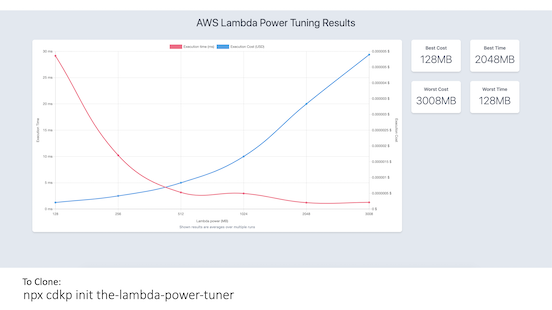
The Lambda Power Tuner
Use the Lambda Power Tuner state machine to work out the optimum configuration settings for your Lambda Function.
2 / Measure and optimize function startup time:
Evaluate function startup time for both performance and cost.
The X-Ray Tracer
Learn about using AWS X-Ray for tracing events through your system. This pattern has X-Ray enabled on API Gateway, Lambda, DynamoDB, External HTTP calls, SNS and SQS
3 / Take advantage of concurrency via async and stream-based function invocations:
Functions can be executed synchronously and asynchronously. A functions’ concurrency model can be better used via asynchronous and stream-based invocations. Queues, streams, or events can be aggregated resulting in more efficient processing time per invocation rather than invocation per request-response approach.
The Big Fan
Uses SNS to fan out Async messages between multiple consumers

The Destined Lambda
Combine Lambda Destinations with EventBridge to build an event driven system

The EventBridge ATM
Build an event driven ATM with different rules to route events

The EventBridge ETL
Build a fully serverless, event driven CSV to DynamoDB pipeline
4 / Optimize access patterns and apply caching where applicable:
Consider caching data that may not need to be frequently up-to-date, and optimize access patterns to only fetch data that is necessary to end users.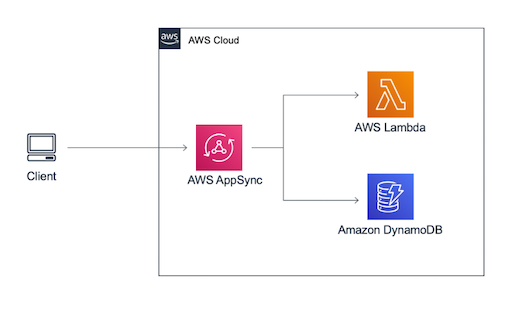
The Simple GraphQL Service
Simple graphQL service built with AppSync. Allows UIs to specify exactly what data they want.
5 / Integrate with managed services directly over functions when possible:
Consider using native integration between managed services as opposed to functions when no custom logic or data transformation is required.
The Big Fan
API Gateway directly integrated with SNS via VTL, removing the need for a Lambda Function.
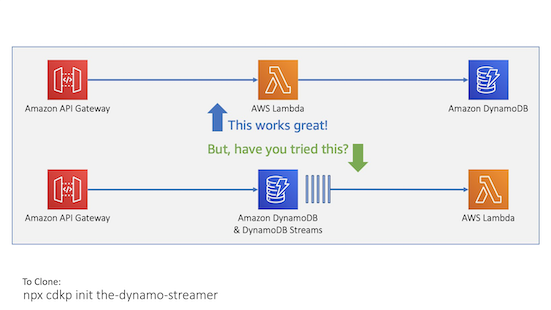
The Dynamo Streamer
You can integrate API Gateway directly with DynamoDB, this removes an unnecessary Lambda Function.

COST 1: How do you optimize your costs?
Design, implement, and optimize your application to maximize value. Asynchronous design patterns and performance practices ensure efficient resource use and directly impact the value per business transaction.
AWS DocsAWS Best Practices
1 / Minimize external calls and function code initialization:
Functions may call other managed services and third-party APIs to operate as intended. Functions may also use application dependencies that may not be suitable for ephemeral environments. Reviewing and optimizing both can directly impact on value provided per invocation.2 / Optimize logging output and its retention:
Review logging level, logging output, and log retention to ensure that they meet your operational needs. This helps prevent unnecessary logging and data retention while ensuring that you have the minimum levels necessary for workload operation.3 / Optimize function configuration to reduce cost:
Functions unit of scale is memory where CPU, Network and I/O are proportionately allocated. Consider benchmarking and reviewing whether you are under/overutilising what your function is allocated to. Benchmark your Lambda function execution with various memory settings as under some conditions the added Memory/CPU may lower the duration and with this new combination reduce the cost of each invocation.
The Lambda Power Tuner
Use the Lambda Power Tuner state machine to work out the optimum configuration settings for your Lambda Function.
